🐸 CIPHERS 🐸
encryption & decryption
Welcome to the world of encrypting and decrypting ciphers! Slides can be found with this link
🔑 ROT13 CIPHER 🔑
The ROT13 cipher is a substitution cipher where each letter is replaced by the letter 13 places down the alphabet. It is a special case of the Caesar cipher with a shift of 13.
How It Works
- Replace each letter with the letter 13 positions down the alphabet.
- Wrap around to the beginning of the alphabet if necessary.
- Applying ROT13 twice returns the original text.
- USE YOUR CIPHER WHEEL!
Decrypting ROT13 Ciphers
task
Decrypt the following ciphers. Note that punctuation matters when inputting your answers. Upper and lower case does not matter.
The following all use the ROT13 cipher.
Cipher 1
Qvq lbh xabj... Cvenpl jnf na rkgerzryl pbzcrgvgvir ohfvarff. Cvengrf jbhyq bsgra wbva sbeprf jvgu bar nabgure, sbezvat nyyvnaprf naq syrrgf, va beqre gb vapernfr gurve punaprf bs fhpprff naq znkvzvfr gurve cebsvgf.
Cipher 2
Va gur pnaqyryvg unyyf bs Ubtjnegf, frpergf geniry snfgre guna bjyf, naq rirel juvfcre pneevrf gur jrvtug bs zntvp naq zvfpuvrs.
🔒 CAESAR CIPHER 🔒
The Caesar cipher is a substitution cipher where each letter in the plaintext is shifted by a fixed number of places down the alphabet.
How It Works
- Choose a shift value (e.g., 3).
- Replace each letter with the letter that is
shiftpositions down the alphabet. - Wrap around to the beginning of the alphabet if necessary.
- USE YOUR CIPHER WHEEL!
Decrypting Caesar Ciphers
task
Decrypt the following ciphers. Note that punctuation matters when inputting your answers. Upper and lower case does not matter.
The following all use a Caesar cipher with different shift values.
Cipher 1
Y qcapcr kcqqyec uyq upgrrcl ml rfc uyjjq md rfc aytcpl, uygrgle dmp qmkcmlc ajctcp clmsef rm qmjtc gr.
Cipher 2
Oek adem jxqj vuubydw oek wuj mxud oekhu ijqdtydw yd q xywx fbqsu... ikttud khwu je zkcf?... Y tedj xqlu yj. - Sqfjqyd Zqsa Ifqhhem.
Cipher 3
Liztqvo, pwtl ug pivl. Vwbpqvo jmiba i Rmb bew pwtqlig, ivl zqopb vwe gwc kiv aidm nqnbg xwcvla xmz xmzawv. Bpiba bew pcvlzml xwcvla wnn nwz i niuqtg wn nwcz.
🕵️ SUBSTITUTION CIPHERS 🕵️
Substitution ciphers are where one character is replaced by another character.
Frequency & Word Analysis
Decryption helper website Decryption helper website from the lecture
breaking substitution ciphers tips
- Look for one/two letter words
- Look for apostrophes
- Look for repeating letters
- Use the above website to analyse the frequency of words and compare against common letters
Decrypting Substitution Ciphers
task
Decrypt the following ciphers. Note that punctuation matters when inputting your answers. Upper and lower case does not matter.
The following all have different cipher keys.
Cipher 1
VJIF RPF GJPY XPFRE, VJIF RKDAFLF XPFREYFVV, RYH VJIF DRLF XPFREYFVV EDPUVE UNJY EDFI.
Cipher 2
HM'S V UZRRI MKHRW, VQCHMHJR. HM NVR MVPT JRT MJ SZCOHQT KTHWKMS JG KVGGJLHRW YTXMKS. VRY SJQTMHQTS MKTI VGT JRT VRY MKT SVQT.
Cipher 3
DST HTEIFL YEEC TEIC WNOCE WE'TE OK VNEF. OV'L DKCP WNEK WE WIBE WE TEICOLE VNOKML WETE LVTIKME.
🧩 Vigenere Ciphers 🧩
A Vigenere Cipher is like a substitution cipher, except that we use a different rotation for every letter.
Usually these are based off a phrase or word.
Try encrypting/decrypting
Vigenere Cipher encryption/decryption
breaking vigenere ciphers tips
- It's really hard!
- We won't be covering much breaking of them, but feel free to try the following if you have time.
- Try using techniques from substitution ciphers, with the knowledge that the keys are four letters long.
Examples
Attempt if you dare!
- G xuzc fa vm fa rmybrjgn lmdwhfabh yzp wyhq usz! Fwge ytqemvc ue hsbqg jazv ra majai icotcgcgtq.
- O pir ibcrz gw xka! Wrk ges zuzik swyx sqzk fqb yrdit rqkng vmtr bit.
ASYMMETRIC ENCRYPTION & RSA
What Makes It Asymmetric?
- In symmetric encryption, the same key is used to both encrypt and decrypt.
- For instance, in the Ceaser Ciphers covered earlier, we use the same key to encrypt (shift forwards) and decrypt (shift backwards).
- In asymmetric encryption, there are two different keys:
- Public key: used to lock (encrypt) the message 🔓
- Private key: used to unlock (decrypt) the message 🔑
We call it asymmetric since the keys are not the same for encrypting and decrypting.
This means you can safely share your public key with the world, while keeping your private key secret.
Why Do We Need RSA?
- Symmetric ciphers (like Substitution or Caesar) need both people to share the same secret key.
- But how do we share that key securely over the internet?
- This is a big problem for symmetric encryption schemes.
- RSA solves this by letting you publish your public key so anyone can encrypt messages to you.
- Only your secret private key can decrypt it.
How Does RSA Work? (Simplified)
- Pick two prime numbers (For this example we will use 5 and 11)
- Multiply them together (n = 5 × 11 = 55).
- Choose a public exponent (we will choose e = 3).
- Work out a private exponent (this is quite difficult to do but in this case, d = 27 will work).
- We will chose 9, as our message.
- To encrypt: Raise message to the public exponent, then mod by 55. c = (9^3 mod 55) = 14
- To decrypt: Raise ciphertext to the private exponent, mod by 55. m = (14^27 mod 55) = 9 which was our message!
Practice Task
Task 1: Encryption
Bob’s RSA public key, n = 55 and public exponent, e = 3. Alice wants to send him the message, m = 4. What is the ciphertext? (encrypted message)
Try to solve before opening the answer!
Show Answer
Step 1: formula
ciphertext = message^e mod n
Step 2: plug in numbers
ciphertext = 4^3 mod 55
Step 3: calculate the power
4^3 = 64
Step 4: calculate 64 mod 55
64 mod 55 = 9
Ciphertext = 9
Task 2: Decryption
Bob’s private key, d = 27 and public exponent, n = 55. He receives ciphertext, c = 9. What is the hidden message, m? Hint (use this calculator for large values: https://www.wolframalpha.com)
Try to solve before opening the answer!
Show Answer
Step 1: formula
message = ciphertext^d mod n
Step 2: plug in numbers
message = 9^27 mod 55
Step 3: calculate the power (we will need a powerful online calculator like wolfram alpha:
https://www.wolframalpha.com/input?i=9%5E27)
9^27 = 58149737003040059690390169
Step 4: calculate 58149737003040059690390169 mod 55 (we will also use wolframalpha: https://www.wolframalpha.com/input?i=58149737003040059690390169+mod+55)
58149737003040059690390169 mod 55 = 4
Decrypted message = 4
This is the first page of the section about Breaking Game Saves
1: Locating Save Files
In this section you will learn to:
- Use the inspect element to find save files
- Use the export and import features in games
1.2: Using Import and Export
Some games make it super easy to locate a save file, as they want people to be able to use different saves. This will typically work by having a way to "Export" and "Import" the current save file.
To check for this, look in the settings of the game for an option that looks like:
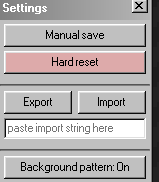
Pressing the "export" button here will typically copy something to our clipboard, or download a file that we can use later with cyberchef.
To use a save file, try pressing the "import" option, which should prompt us to upload a file, or paste something into a box.
2: Decoding & Encoding Save Files
In this section you will learn to:
- Decode save files into an editable format
- Use cyberchef
- Encode decoded save files
Part 2.1: Using Cyberchef
Cyberchef (https://gchq.github.io/CyberChef/) is a great tool for simple decoding/encoding tasks.
It comes with a list of "Operations" we can combine into a "Recipe" to decode or encode text.
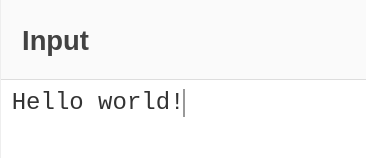
For example, to encode "Hello, world!" using Base64, we can:
- Type our text into the "Input" box:
- We can then use the search box on the left-hand side to find the "To Base64" operation.
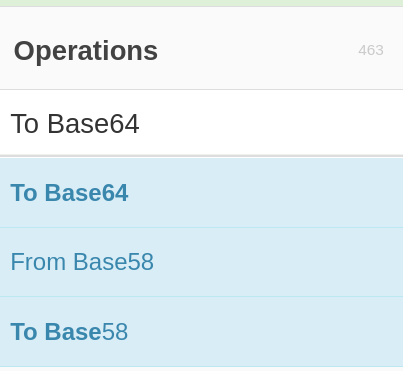
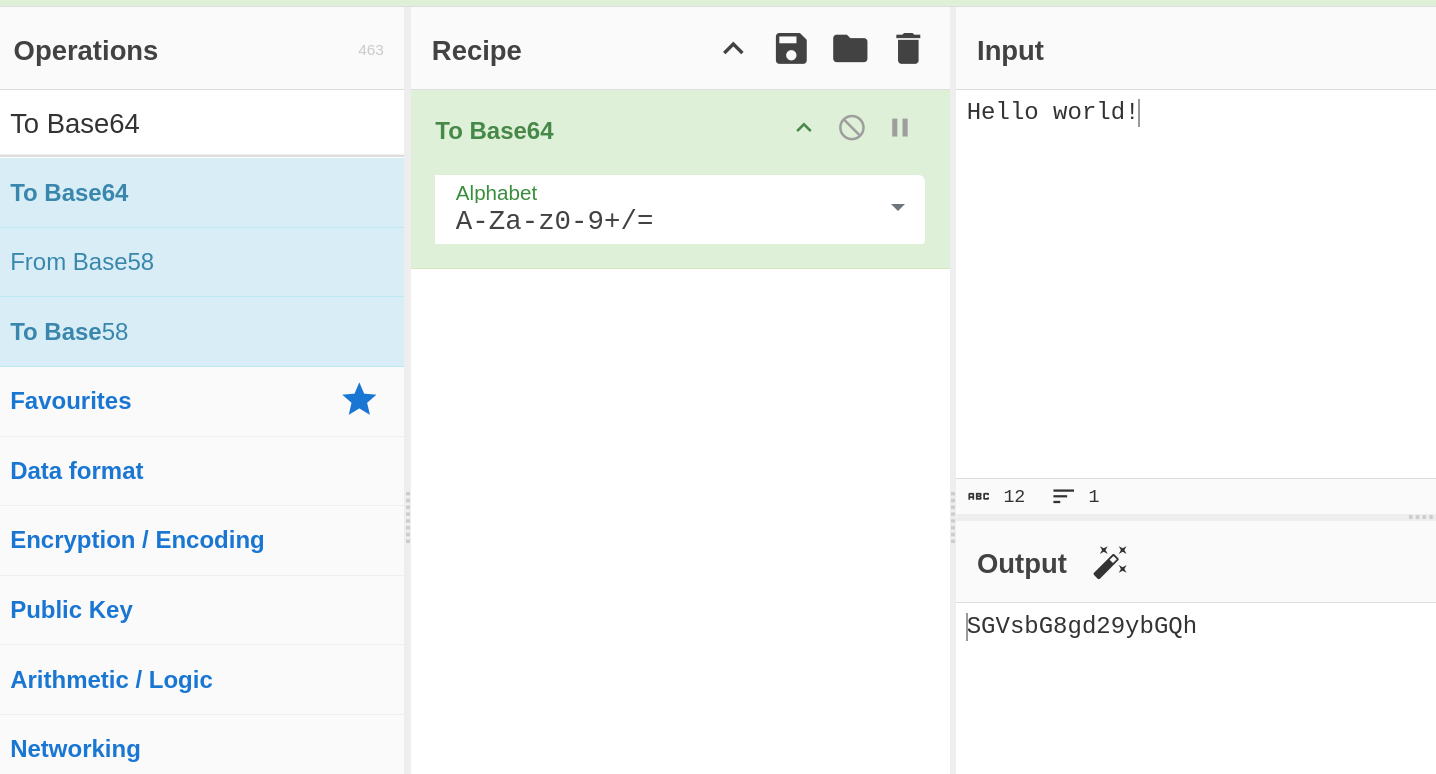
- We can then drag the operation into the "Recipe" section to make the recipe.
This will then run the recipe on our text, and we can see the encoded/decoded text in the "Output" section
Part 2.2: Decoding With CyberChef
When given a save file, if it is not in a readable format, we can try decoding with cyberchef!
- To do this, first paste your save file into the input box.
If your save file is a file on your computer, press "Open file as input":
Next, find the save file and double click it (or press open). This will place the file into input for you.
- Now, we can guess the operation that will decode our text. Some typical encodings are "Base64" and "Zlib". "Decoding" operations typically have some word like "From" or "Inflate" in the operations.
If you are struggling, you can try the "Magic" operation, which will give you a hint for what encoding may be used.
- Repeat step 2, adding more operations to the recipe until we can read the text in the "Output" section!
2.3: Encoding with Cyberchef
After decoding and modifying our save file, we will need to encode the save file before the game we were playing can use it.
For example, if a game's save file was originally encoded in base64, the game will only accept new saves that use base64.
In cyberchef, this means we will need to encode our modified save file using the opposite recipe of how we decoded it.
We can do this like:
- For every operation in our recipe, find the opposite operation using the search feature, and replace it using the opposite operation.
Some common examples may be:
- From Base64 becomes To Base64
- Zlib inflate becomes Zlib deflate
- Unzip becomes Zip
- Then reverse the order of the operations - if your recipe was:
- From Base64
- Zlib inflate
After reversing each operation and their order, we should have the recipe
- Zlib deflate
- To Base64
The encoded save file should now be in the "Output" section, ready for use!
Data Compression
Why Compress Save Files?
Data compression is simply the process of shrinking a file to make it smaller. Game developers do this for a few reasons:
- Saving Disk Space: A smaller save file takes up less storage.
- Faster Loading and Saving: Smaller files can be read and written much faster, leading to quicker save and load times in the game.
- Hiding Data: Compressed data is not readable. This stops users from opening the save file in a text editor and easily changing the file content.
How to Identify Compressed Files
A computer needs a way to know what kind of file it's reading. It doesn't look at the file extension (like .zip). Instead, it reads the first few bytes of the file itself, called the header. The most important part of the header is the first 2 to 4 bytes, called the File Signature (or Magic Number).
info
You can find the signature by using the To Hex recipe in CyberChef and looking at the very first bytes in the output.
tip
If the data looks like a total mess of random symbols, that's a strong hint it might be compressed!
Common Compression Formats
| Format Name | CyberChef Recipe (to decompress) | Signature (Magic Number) | Description |
|---|---|---|---|
| Raw Deflate | Raw Inflate | (none) | Compressed data with no header or any extra info. |
| Zlib | Zlib Inflate | 78 01, 78 9C, 78 DA | Compressed data wrapped with a small Zlib header. |
| Gzip | Gunzip | 1F 8B | Compressed data with a Gzip header. |
| Zip archive | Unzip | 50 4B 03 04 | An archive designed to hold one or more files. |
important
Raw Deflate is just the pure compressed data itself, with no magic numbers. This is the compression used in the Clicker Heroes' save file.
Guide
note
Here is the process you will need to follow when you find a compressed save file:
- Use the
To Hexrecipe in CyberChef to find the File Signature (magic number) at the start of the data.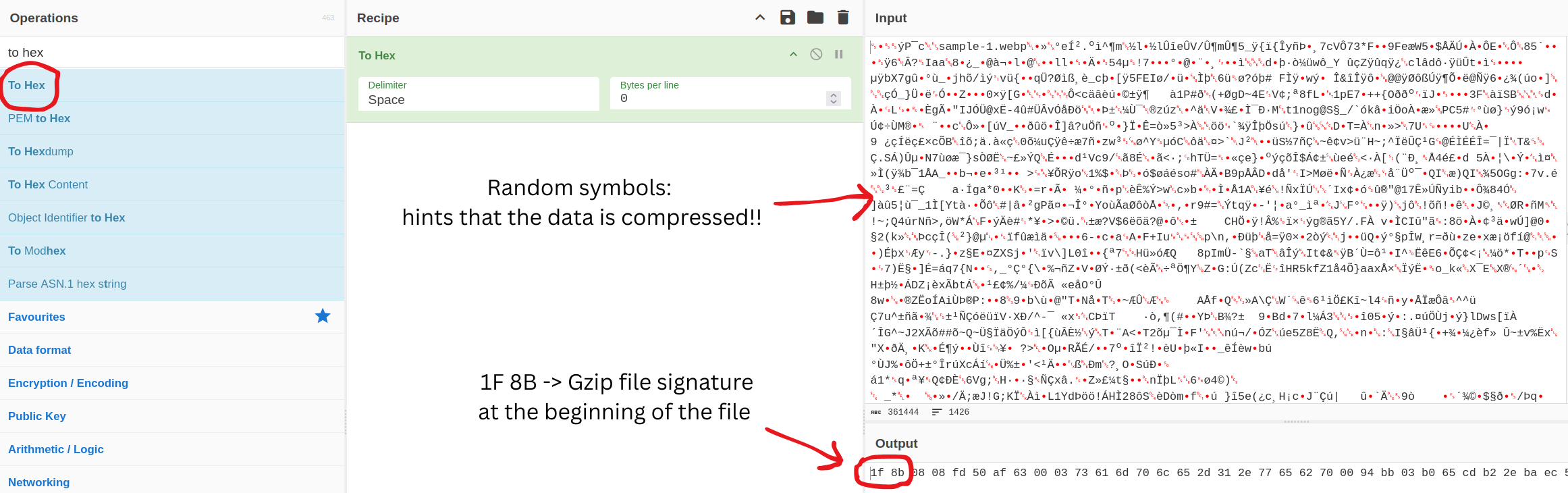
- Look up the signature in the Cheat Sheet above to find the correct CyberChef recipe.
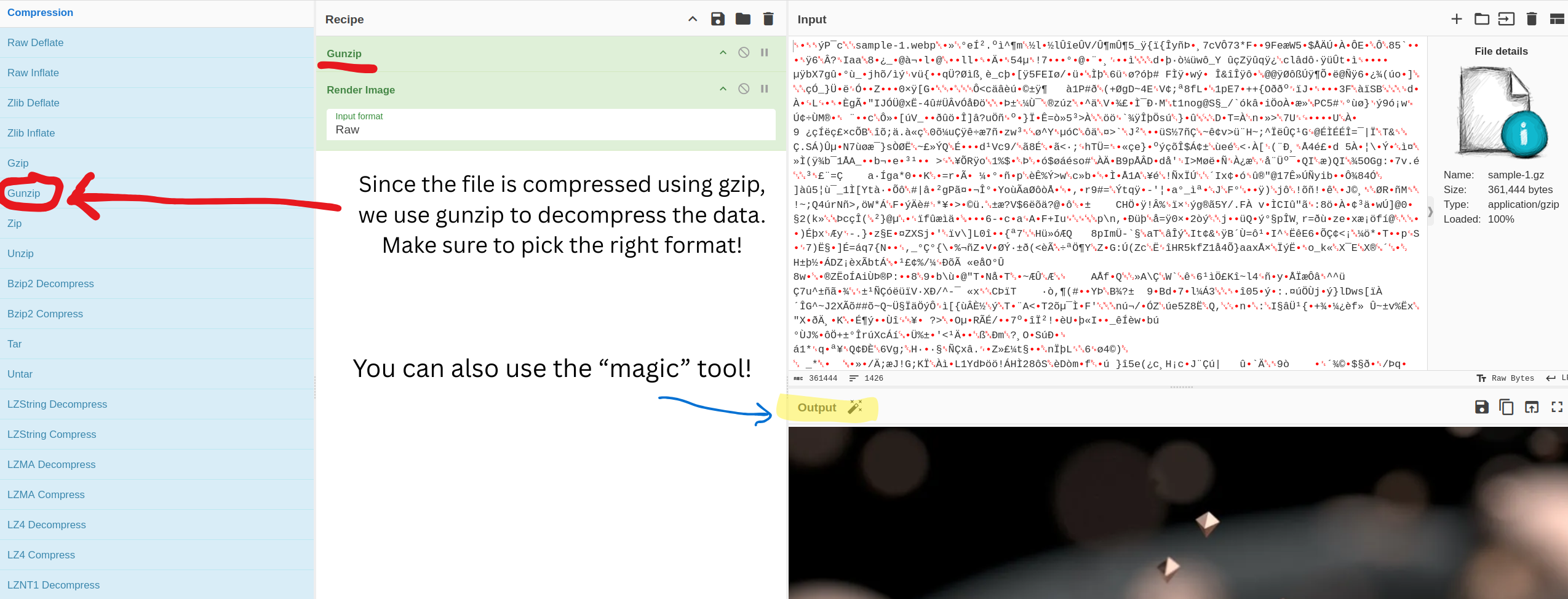
- Inspect the output: After decompressing, the data should now be readable (like JSON or plain text).
- Edit the file. Change the values to whatever you want!
- Encode it back. You need to re-compress your edited data so the game can read it (see section
1.2.3: Encoding Save Filesfor more information). - Load your new save file to see your changes! 🥳🎉🎉
🕸️ DAY 3 - Web Attacks
Cookies
what are cookies?
Cookies are a small piece of data that browsers use to identify you. It allows it to remember information like your browsing history, shopping cart items, whether you were logged in or not, and site preferences, and are not necessarily bad.
Cookies can sometimes store a special kind of token (JWT tokens), like a special id that is used for authentication. If you could somehow trick the computer to think you are someone else, then you could gain access to their account.
There are 3 main parts of a JWT.
Each JWT can be split into 3 main parts.
- Header
- Contains metadata.
- The type of the JWT token.
- Payload
- The main user data that is being sent.
- Contains certain key-value pairs, like 'isadmin': true
- Signature
- The 'password' that is being sent with the token, that is used to verify that the token hasn't been modified.
how to decode a cookie?
Say we have a token like eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImNvbnJhZCIsImlhdCI6MTc1OTU4MTk1NywiZXhwIjoxNzU5NTg1NTU3fQ.RUjnxcJ_NhGWGqeEQvisgzF5jeRgL7o1ROynocUX-c0
- First, paste the token into the token field in this decoding tool
- Modify the payload. Notice how the entire token changes even with a very small change.
- Copy the changed token and paste it back into the browser. (Right click, Inspect, Storage, Cookies, and click on the value field of the token. )
tasks
- The tasks for this activity is to exploit this to gain access to a user profile on the pirate website.
- How might we use the steps above to help us?
IDOR
what is idor?
IDOR stands for Insecure Direct Object Reference and it is a type of vulnerability that occurs when websites use user-provided input without first doing some checks.
How IDOR Works
IDOR vulnerabilities typically occur when an application does not check the user has access to a certain thing before giving them access. This can be very dangerous.
examples
For example, consider a url that you may have seen before in the past:
www.examplewebsite.com/orders/123
If the application doesn't verify that the current user is authorized to view order #123, an attacker could simply change the number to access other users' orders: Like this:
www.examplewebsite.com/orders/124www.examplewebsite.com/orders/125www.examplewebsite.com/orders/1
IDOR vulnerabilities can be found in various contexts:
- User profiles:
/user/profile?id=456 - File downloads:
/download?file=document123.pdf - API endpoints:
/api/users/789/messages - Database records:
/invoice?invoice_id=ABC123 - Support tickets:
/ticket/14
tasks
- Find out what page could potentially lead to what we just mentioned.
- After you discover the vulnerability, see what you can do with it. What additional information can you find out?
LocalStorage
what is local storage?
You can think of local storage as a place that your browser stores small pieces of information about you, locally. It is typically used to store small pieces of information, like your user preferences (whether you are using dark mode or not 😈), and IDs.
Local storage stores data in the form of key - value pairs. You can think of this like a name tag associated with each value. Whenever you are trying to look for something, all you need to know is the name tag!
but what are some of the issues of this?
- Anybody can manipulate local storage. Cannot store any sensitive information.
- Size limitation - Can only store 5MB.
- Possibility of leaking sensitive information.
- Cross site scripting attacks
tasks.
- Your task is to exploit the local storage on the website.
- Firstly, how do you navigate to where you can view local storage? (Hint: Right click!)
- Then, what can you do with the data that is being stored there. What format is it in? Can you modify it?
SQL Injection
what is sql injection?
SQL Injection is another form of vulnerability that attacks the database.
What is SQL?
SQL stands for Structured Query Language, and you can think of it as another programming language that allows us to get information out of a 'database'.
Think of a database like a giant dictionary. You can look things up, and pull information. Say you wanted to look up 'all the words that began with the letter K'. This is something that you could do with SQL.
The issue begins when we perform queries like 'Give me all the users that ...' and the user is able to inject their custom phrases into that sentence. For example, the attacker might say 'have a username of 'bob''. Then, without checking, the computer would execute the query 'Give me all the users that have a username of bob'.
common sql injection patterns
Here is the most common SQL Injection pattern... This may come in handy for the tasks.
' OR '1'='1'
tasks
- On the website, you are to find where you could possibly use SQL Injection. What are some common places that these vulnerabilities are found?
